Phishing email messages, websites, and phone calls can be carried out for the purposes of stealing credentials, in order to steal money, defame sites, and any number of other reasons. Attackers can do this by sending malicious software to your computer in the hopes of getting you to run it, or by tricking you into sending personal or sensitive information (such as passwords and other credentials).
Cybercriminals also use social engineering to trick you into running such programs or send such information. They may email, call, text or try to get you to download files from a website. Phishing emails can take many forms, but generally they will present some false pretence as to why they are entitled to the information, or have the authority to get you to do what they need you to.
Here is an example of what one may look like:

Some key things to look for are:
- Grammar and spelling: Large companies will almost never allow correspondence to go out without spell-checking it. If you see a spelling mistake you should be suspicious.
- Links: Beware of links in emails, if something seems wroung to you, hover your mouse over the link for a second. The address shown below the cursor will show the actual destination of the link, if it is not from the same domain as the sender claims to be from, be suspicious
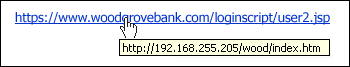
- Coercion: Reputable sites rarely coerce their customers, if an email sender attempts to use a threat of coercion to do something, they may want you to do it for nefarious purposes.
- Spoofing: Scammers often use graphics in email that, whilst looking legitimate, can take you to sites which utilise pop-ups or have slightly different domains to the legitimate ones.
If you see one of these emails, do not respond to them, instead, look up the site they claim to be representing, and find a real email address on the site to alert them of the threat.

